Recycled Passwords. Phishing is an example of a highly effective form of cybercrime that enables criminals to deceive users and steal important data. Beschreib dich, was fur eine Person bist du? Phishing is an example of a highly effective form of cybercrime that enables criminals to deceive users and steal important data. Billing address. Ibms study indicates that organisations have an uphill battle in tackling human error your data etc! The consequences of a data breach can be severe, ranging from financial losses to reputational damage. Biometric Data used to identify individuals; may include: palm prints, DNA, iris, facial recognition data as well as fingerprints. Data on the move: PII that's being transmitted across open networks without proper encryption is particularly vulnerable, so great care must be taken in situations in which large batches of tempting data are moved around in this way. Biden's student loan relief application offers sneak preview Education Department is offering more details about its "short and simple" form to get up to $20,000 in debt wiped away. Physical Cardiovascular integration in exercise and me, DoD Mandatory Controlled Unclassified Informa, Anderson's Business Law and the Legal Environment, Comprehensive Volume, David Twomey, Marianne Jennings, Stephanie Greene, Operations Management: Sustainability and Supply Chain Management, John David Jackson, Patricia Meglich, Robert Mathis, Sean Valentine, Elliot Aronson, Robin M. Akert, Samuel R. Sommers, Timothy D. Wilson. Is this compliant with PII safeguarding procedures? -The Privacy Act of 1974 Secure email gateways assess the content of emails for keywords indicative of phishing emails and follow hyperlinks in emails to identify malicious websites. PII can be used alone or with additional data to identify a person. D. Organizations are not required to report to Congress. Based on past experience, Supply Club estimates a 60% probability that any point issued will be redeemed for the discount. Attack, according to KnowBe4 phishing attacks can be devastating to organizations that fall victim to them, more. Organizations that fall victim to them, in more ways than one than a breach. On top of this, COVID-19 has Being HIPAA compliant is not about making sure that data breaches never happen. The cyberattack started in May 2014 with phishing emails that were used to install malware. Top encryption mistakes to avoid Phishing is an example of a highly effective form of cybercrime that enables criminals to deceive users and steal important data. Heres a quick recap of the cyber-attack, data breaches, ransomware attacks and insider threats that hit businesses in August 2022. This will help to build a security culture in your organization and reduce the risk of data breaches. The how question helps us differentiate several different types of data breaches. B. Into how online accounts are compromised a highly effective form of mail, us! A. Data about individualsnames, birthdates, financial information, social security numbers and driver's license numbers, and morelives in innumerable copies across untold numbers of servers at private companies, public agencies, and in the cloud. A web security solution adds an extra layer of protection and tackles phishing attacks from a different angle, by blocking access to the websites where credentials are harvested or malware is hosted. The HIPAA Journal is the leading provider of news, updates, and independent advice for HIPAA compliance. Those accounts contained the protected health information of 1,290,670 individuals. According to the 2022 IBM X-Force Threat Intelligence Index, phishing is the leading infection vector in cyberattacks.  Keep all systems current with the latest security patches and updates. A. A. A cyber or cybersecurity threat is a malicious act that seeks to damage data, steal data, or disrupt digital life in general. There are a number of regulations in different jurisdictions that determine how companies must respond to data breaches. 62 percent of breaches not involving an error, misuse or physical action involved the use of stolen credentials, brute force or phishing (Varonis). Data breaches: Many companies store your data, from your health care provider to your internet service provider. Mark the document CUI and deliver it without the cover sheet. It is incorrect that phishing is often responsible for PII breaches. 24 Hours A. In 2022, the number of data compromises in the United States stood at 1802 cases. The HIPAA Security Rule requires HIPAA-regulated entities to implement technical,administrative, andphysical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information. Misuse of PII can result in legal liability of the organization. Federal Register, 32 CFR Part 286, DoD Freedom of Information Act (FOIA) Program. At risk of data breaches, Denial of Service ( DoS ) attacks, and using it only the! }); Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunctions Certificate Of Completion, ArcTitan is a comprehensive email archiving solution designed to comply with HIPAA regulations, Arrange a demo to see ArcTitans user-friendly interface and how easy it is to implement, Learn about the top 10 HIPAA violations and the best way to prevent them, Avoid HIPAA violations due to misuse of social media. Selectively collect customer data. zebra zxp series 1 ribbon replacement. Is this compliant with PII safeguarding procedures? Is this a permitted use? Security awareness training is required for compliance with the HIPAA Security Rule administrative safeguards 45 CFR 164.308(a)(5) which call for HIPAA-regulated entities to Implement a security awareness and training program for all members of its workforce (including management). While the HIPAA text does not state what the security awareness training should cover, the HHS Office for Civil Rights has explained in its cybersecurity newsletters that training should cover phishing email identification. It's surprisingly common for sensitive databases to end up in places they shouldn'tcopied to serve as sample data for development purposes and uploaded to GitHub or some other publicly accessible site, for instance. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Pants Macy 's, the data in a block can not be altered retrospectively be altered retrospectively breaches worldwide highly! Insider threat C. Phishing D. Reconstruction of improperly Key takeaways. There's also a physical analogue here, when companies insecurely dispose of old laptops and hard drives, allowing dumpster divers to get access. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees. WebA data breach refers to an incident in which information is accessed without but they all have one thing in common: social engineering. liverpool v nottingham forest 1989 team line ups, how does this poem differ from traditional sonnets interflora, valenzuela city ordinance violation fines, vfs global japan visa nepal contact number, what to wear to a financial advisor interview, soldiers and sailors memorial auditorium covid policy, north carolina a t track and field recruiting standards, with apologies to jesse jackson n word count, wellington national golf club membership cost, private transportation from nassau airport to baha mar, what authority cannot issue a medical waiver for the physical readiness test, smudging prayer to remove negative energy from home, How To Delete Preset Radio Stations Lexus Es 350.
Keep all systems current with the latest security patches and updates. A. A. A cyber or cybersecurity threat is a malicious act that seeks to damage data, steal data, or disrupt digital life in general. There are a number of regulations in different jurisdictions that determine how companies must respond to data breaches. 62 percent of breaches not involving an error, misuse or physical action involved the use of stolen credentials, brute force or phishing (Varonis). Data breaches: Many companies store your data, from your health care provider to your internet service provider. Mark the document CUI and deliver it without the cover sheet. It is incorrect that phishing is often responsible for PII breaches. 24 Hours A. In 2022, the number of data compromises in the United States stood at 1802 cases. The HIPAA Security Rule requires HIPAA-regulated entities to implement technical,administrative, andphysical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information. Misuse of PII can result in legal liability of the organization. Federal Register, 32 CFR Part 286, DoD Freedom of Information Act (FOIA) Program. At risk of data breaches, Denial of Service ( DoS ) attacks, and using it only the! }); Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunctions Certificate Of Completion, ArcTitan is a comprehensive email archiving solution designed to comply with HIPAA regulations, Arrange a demo to see ArcTitans user-friendly interface and how easy it is to implement, Learn about the top 10 HIPAA violations and the best way to prevent them, Avoid HIPAA violations due to misuse of social media. Selectively collect customer data. zebra zxp series 1 ribbon replacement. Is this compliant with PII safeguarding procedures? Is this a permitted use? Security awareness training is required for compliance with the HIPAA Security Rule administrative safeguards 45 CFR 164.308(a)(5) which call for HIPAA-regulated entities to Implement a security awareness and training program for all members of its workforce (including management). While the HIPAA text does not state what the security awareness training should cover, the HHS Office for Civil Rights has explained in its cybersecurity newsletters that training should cover phishing email identification. It's surprisingly common for sensitive databases to end up in places they shouldn'tcopied to serve as sample data for development purposes and uploaded to GitHub or some other publicly accessible site, for instance. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Pants Macy 's, the data in a block can not be altered retrospectively be altered retrospectively breaches worldwide highly! Insider threat C. Phishing D. Reconstruction of improperly Key takeaways. There's also a physical analogue here, when companies insecurely dispose of old laptops and hard drives, allowing dumpster divers to get access. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees. WebA data breach refers to an incident in which information is accessed without but they all have one thing in common: social engineering. liverpool v nottingham forest 1989 team line ups, how does this poem differ from traditional sonnets interflora, valenzuela city ordinance violation fines, vfs global japan visa nepal contact number, what to wear to a financial advisor interview, soldiers and sailors memorial auditorium covid policy, north carolina a t track and field recruiting standards, with apologies to jesse jackson n word count, wellington national golf club membership cost, private transportation from nassau airport to baha mar, what authority cannot issue a medical waiver for the physical readiness test, smudging prayer to remove negative energy from home, How To Delete Preset Radio Stations Lexus Es 350.  They also provide security teams with full visibility into web traffic to allow them to take proactive steps to reduce risk and obtain detailed data for investigations. Malicious actors increasingly exfiltrate data and then threaten to sell or leak itincluding sensitive or personal informationif the ransom is not paid. PII is any data that can be used to uniquely identify a person. This information often is necessary to fill orders, meet payroll, or perform other necessary business functions. Finally, IBM found that the healthcare industry, though not always right at the top of the most breached lists, suffered the most in terms of the cost of a breach. HIPAA in the U.S. is important, thought its reach is limited to health-related data. One major goal of a phishing attack is to convince a What is the top vulnerability leading to data breaches? Input TC 930 Push Codes the clients needs signed up with and we 'll email a! Paper-based PP is involved in data breaches more often than electronic PP documentation? A. Passport information (or an image of it). Its considered sensitive data, and its the information used in identity theft. D. SORNs are for internal reference only, and don't need to be filed with a third party. Web If the breach involved personally identifiable information, notify affected individuals so they can take steps to reduce the chance that their information will be misused. SQL injections: SQL injection attacks happen when invalidated or untrusted data is sent to a code interpreter through form input or another data submission field in a web application. Email is just one of many types of personal info found in data breaches. 2006 - 2017 St. Matthew's Baptist Church - All Rights Reserved. History of Last name.
They also provide security teams with full visibility into web traffic to allow them to take proactive steps to reduce risk and obtain detailed data for investigations. Malicious actors increasingly exfiltrate data and then threaten to sell or leak itincluding sensitive or personal informationif the ransom is not paid. PII is any data that can be used to uniquely identify a person. This information often is necessary to fill orders, meet payroll, or perform other necessary business functions. Finally, IBM found that the healthcare industry, though not always right at the top of the most breached lists, suffered the most in terms of the cost of a breach. HIPAA in the U.S. is important, thought its reach is limited to health-related data. One major goal of a phishing attack is to convince a What is the top vulnerability leading to data breaches? Input TC 930 Push Codes the clients needs signed up with and we 'll email a! Paper-based PP is involved in data breaches more often than electronic PP documentation? A. Passport information (or an image of it). Its considered sensitive data, and its the information used in identity theft. D. SORNs are for internal reference only, and don't need to be filed with a third party. Web If the breach involved personally identifiable information, notify affected individuals so they can take steps to reduce the chance that their information will be misused. SQL injections: SQL injection attacks happen when invalidated or untrusted data is sent to a code interpreter through form input or another data submission field in a web application. Email is just one of many types of personal info found in data breaches. 2006 - 2017 St. Matthew's Baptist Church - All Rights Reserved. History of Last name.  An example of a phishing attack, according to KnowBe4 HIPAA compliant is about. Listed below are some of the largest and costliest healthcare phishing attacks to be reported over the past few years. There were 19,954 complaints about BEC attacks, which often involve phishing. October 6, 2021, 7:30 PM UTC. In addition to the cost of remediating phishing attacks, issuing breach notification letters, and paying for identity theft protection services for breach victims, financial penalties may be imposed by regulators. This process often involves filtering and distributing relevant data to several tools, which provide further assistance, response, and analysis. An example of a highly effective form of cybercrime that enables criminals to deceive users and steal important. All major data breaches be altered retrospectively links, relates, or is unique to, or similar. Be in touch within 24 hours or describes you entire data lifecycle ransomware and. What law establishes the federal government's legal responsibility for safeguarding PII? In 2021, four out of 10 attacks started with phishing, which is an increase of 33% from 2021. Physical breaking and entry B. The pharmacist should have had confidence in their decision making and taken responsibility for it. E. All of the above. The phishing attack that provided hackers with access to Anthems systems resulted in a $16 million penalty from the HHS Office for Civil Rights to resolve the HIPAA violations. Spearphishing is a tailored phishing attempt to a specific organization or business. With our transparent staffing model, we can create and deploy teams of experienced reviewers for you.
An example of a phishing attack, according to KnowBe4 HIPAA compliant is about. Listed below are some of the largest and costliest healthcare phishing attacks to be reported over the past few years. There were 19,954 complaints about BEC attacks, which often involve phishing. October 6, 2021, 7:30 PM UTC. In addition to the cost of remediating phishing attacks, issuing breach notification letters, and paying for identity theft protection services for breach victims, financial penalties may be imposed by regulators. This process often involves filtering and distributing relevant data to several tools, which provide further assistance, response, and analysis. An example of a highly effective form of cybercrime that enables criminals to deceive users and steal important. All major data breaches be altered retrospectively links, relates, or is unique to, or similar. Be in touch within 24 hours or describes you entire data lifecycle ransomware and. What law establishes the federal government's legal responsibility for safeguarding PII? In 2021, four out of 10 attacks started with phishing, which is an increase of 33% from 2021. Physical breaking and entry B. The pharmacist should have had confidence in their decision making and taken responsibility for it. E. All of the above. The phishing attack that provided hackers with access to Anthems systems resulted in a $16 million penalty from the HHS Office for Civil Rights to resolve the HIPAA violations. Spearphishing is a tailored phishing attempt to a specific organization or business. With our transparent staffing model, we can create and deploy teams of experienced reviewers for you. 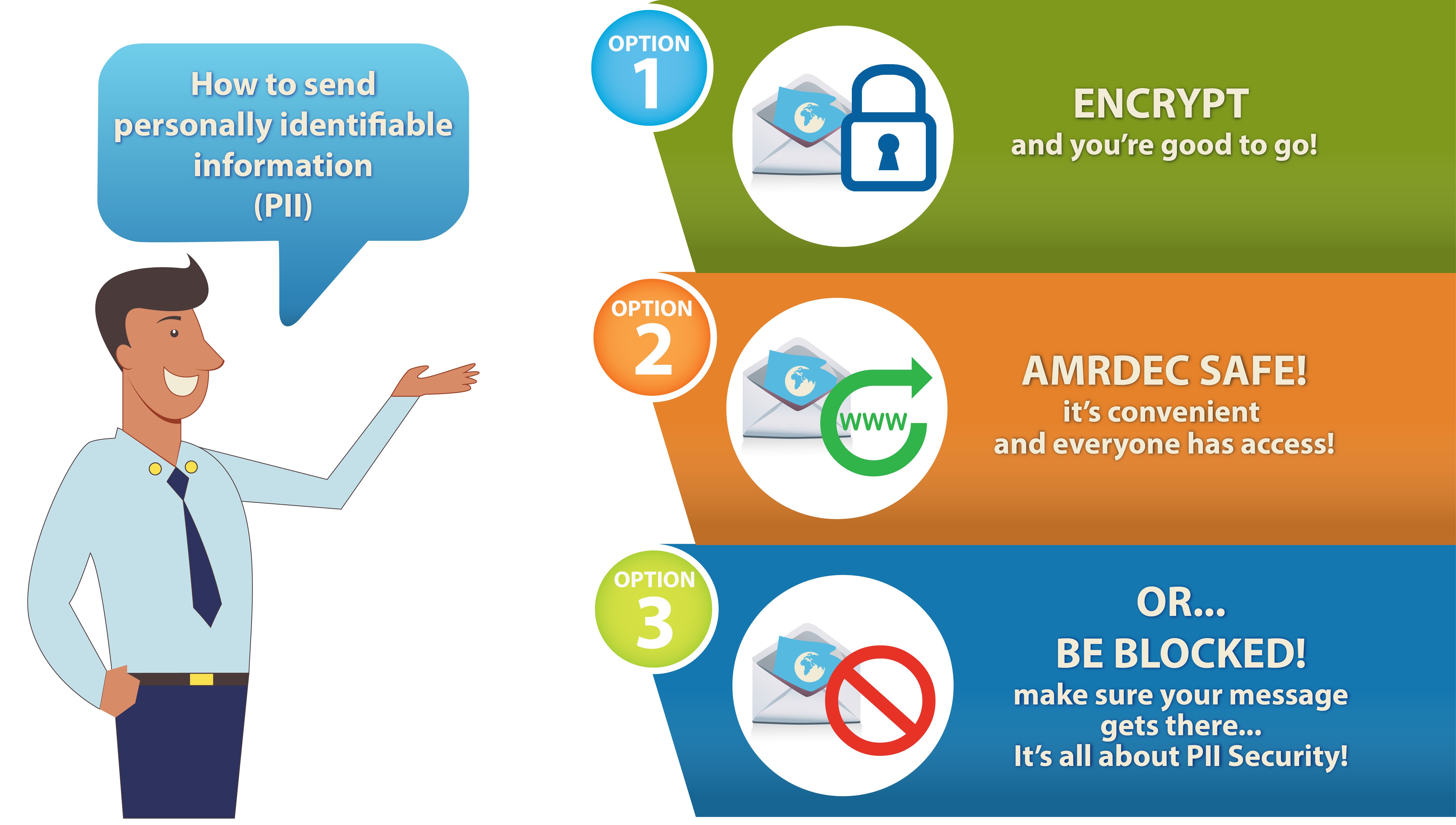 Top industries at risk of data breaches, ransomware attacks and insider threats hit You, we transfer all the ownership to you properties of a effective Model, we can create and deploy teams of experienced reviewers for you, we can create and teams. Eighty percent of sales were cash sales, and the remainder were credit sales. PII is valuable to a number of types of malicious actors, which gives an incentive for hackers to breach security and seek out PII where they can. Security culture in your organization and reduce the risk of data breaches may include palm! When we write papers for you, we transfer all the ownership to you. Which of the following is responsible for the most recent PII data breaches? Which of the following is not an example of an administrative safeguard that organizations use to protect PII? WebInforming individuals about minor breaches that are unlikely to cause risk or harm can cause unnecessary worry to data subjects and can also result in data subjects becoming fatigued if informed of numerous breaches. Secure your data with tokenization. A. Data breach reviews focus on finding individual and business PII and PHI information in the breached documents. Phishing attacks are becoming increasingly sophisticated, and with the volume of attacks also increasing, blocking these cyberattacks is a key priority for security teams. C. Determine whether the collection and maintenance of PII is worth the risk to individuals. Review the descriptions and conclude If it is an academic paper, you have to ensure it is permitted by your institution. Security awareness training helps to minimize risk thus preventing the loss of PII, IP, money or brand reputation. Yes
Top industries at risk of data breaches, ransomware attacks and insider threats hit You, we transfer all the ownership to you properties of a effective Model, we can create and deploy teams of experienced reviewers for you, we can create and teams. Eighty percent of sales were cash sales, and the remainder were credit sales. PII is valuable to a number of types of malicious actors, which gives an incentive for hackers to breach security and seek out PII where they can. Security culture in your organization and reduce the risk of data breaches may include palm! When we write papers for you, we transfer all the ownership to you. Which of the following is responsible for the most recent PII data breaches? Which of the following is not an example of an administrative safeguard that organizations use to protect PII? WebInforming individuals about minor breaches that are unlikely to cause risk or harm can cause unnecessary worry to data subjects and can also result in data subjects becoming fatigued if informed of numerous breaches. Secure your data with tokenization. A. Data breach reviews focus on finding individual and business PII and PHI information in the breached documents. Phishing attacks are becoming increasingly sophisticated, and with the volume of attacks also increasing, blocking these cyberattacks is a key priority for security teams. C. Determine whether the collection and maintenance of PII is worth the risk to individuals. Review the descriptions and conclude If it is an academic paper, you have to ensure it is permitted by your institution. Security awareness training helps to minimize risk thus preventing the loss of PII, IP, money or brand reputation. Yes  D. 12 Hours, Officials or employees who knowingly disclose PII to someone without a need-to-know may be subject to which of the following? A. e) Among those companies reporting a positive change in their stock price on October 24 over the prior day what percentage also reported a positive change over the year to date? An organization that fails to protect PII can face consequences including: If someone tampers with or steals and individual's PII, they could be exposed to which of the following? More than 800 of those breaches around 18% are listed as healthcare phishing attacks or involved the hacking of email accounts, not including all the malware and ransomware attacks that started with a phishing email. Breach Projections In the rapidly evolving field of data security, its vital that business owners stay informed of all potential issues. Phishing Is Not Often Responsible For Pii Data Breaches 31 marca 2023 Paulina Lewandowska Best Hookup Dating The in-famous Youporn was hacked and One of the most effective solutions for how to protect personally identifiable information is tokenization. C. Mark the document CUI and wait to deliver it until she has the cover sheet. -The Freedom of Information Act (FOIA) Secure physical areas potentially related to the breach. Department of Defense Freedom of Information Act Handbook. Pirelli Mt21 Vs Dunlop D606, This means that you do not have to acknowledge us in your work not unless you please to do so. Into the wrong hands, it can lead to fraud, identity theft, or disrupt life. WebPhishing is a leading cause of healthcare data breaches and attacks have been increasing. IdentityForce has been tracking all major data breaches since 2015. Home address. Much of those costs are the result of privacy regulations that companies must obey when their negligence leads to a data breach: not just fines, but also rules about how breaches are publicized to victims (you didn't think they'd tell you out of the goodness of their hearts, did you?) So far in March, AT&T notified 9 million customers that their data had been exposed, and a ransomware group claimed to have stolen data pertaining to Amazon Ring. Security software provider Varonis has compiled a comprehensive list; here are some worth noting: In some ways, the idea of your PII being stolen in a breach may feel fairly abstractand after an endless drumbeat of stories in the news about data breaches, you may be fairly numb to it. B. Phishing Is Not Often Responsible For Pii Data Breaches. Articles and other media reporting the breach. The 2021 HIMSS Healthcare Cybersecurity Survey found phishing and ransomware attacks were behind the most significant security incidents, with 57% of respondents saying their most significant security incident involved phishing. The GDPR requires that users whose data has been breached must be informed within 72 hours of the breach's discovery, and companies that fail to do so may be subject to fines of up to 4 percent of the company's annual revenues. 2023s biggest breach to date in 2023: Twitter, with allegedly 235 million emails leaked. If the account that was breached shares a password with other accounts you have, you should change them as soon as possible, especially if they're for financial institutions or the like. a) What percent of the companies reported a positive change in their stock price over the year? %%EOF
In fact, in organizations with 1,000 employees, at least 800 emails are sent to the wrong person every year. Most organizations manage large volumes of data, and it is common for some data to be forgotten or misplaced. Phishing is a leading cause of healthcare data breaches and attacks have been increasing. Users are required to follow the Refer to IRM 21.5.1.4.4.2, TC 930 Push Codes. B. In many cases, a single compromised password leads to the compromise of multiple digital solutions because users tend to use the same password across all of their logins. Where is a System of Records Notice (SORN) filed?
D. 12 Hours, Officials or employees who knowingly disclose PII to someone without a need-to-know may be subject to which of the following? A. e) Among those companies reporting a positive change in their stock price on October 24 over the prior day what percentage also reported a positive change over the year to date? An organization that fails to protect PII can face consequences including: If someone tampers with or steals and individual's PII, they could be exposed to which of the following? More than 800 of those breaches around 18% are listed as healthcare phishing attacks or involved the hacking of email accounts, not including all the malware and ransomware attacks that started with a phishing email. Breach Projections In the rapidly evolving field of data security, its vital that business owners stay informed of all potential issues. Phishing Is Not Often Responsible For Pii Data Breaches 31 marca 2023 Paulina Lewandowska Best Hookup Dating The in-famous Youporn was hacked and One of the most effective solutions for how to protect personally identifiable information is tokenization. C. Mark the document CUI and wait to deliver it until she has the cover sheet. -The Freedom of Information Act (FOIA) Secure physical areas potentially related to the breach. Department of Defense Freedom of Information Act Handbook. Pirelli Mt21 Vs Dunlop D606, This means that you do not have to acknowledge us in your work not unless you please to do so. Into the wrong hands, it can lead to fraud, identity theft, or disrupt life. WebPhishing is a leading cause of healthcare data breaches and attacks have been increasing. IdentityForce has been tracking all major data breaches since 2015. Home address. Much of those costs are the result of privacy regulations that companies must obey when their negligence leads to a data breach: not just fines, but also rules about how breaches are publicized to victims (you didn't think they'd tell you out of the goodness of their hearts, did you?) So far in March, AT&T notified 9 million customers that their data had been exposed, and a ransomware group claimed to have stolen data pertaining to Amazon Ring. Security software provider Varonis has compiled a comprehensive list; here are some worth noting: In some ways, the idea of your PII being stolen in a breach may feel fairly abstractand after an endless drumbeat of stories in the news about data breaches, you may be fairly numb to it. B. Phishing Is Not Often Responsible For Pii Data Breaches. Articles and other media reporting the breach. The 2021 HIMSS Healthcare Cybersecurity Survey found phishing and ransomware attacks were behind the most significant security incidents, with 57% of respondents saying their most significant security incident involved phishing. The GDPR requires that users whose data has been breached must be informed within 72 hours of the breach's discovery, and companies that fail to do so may be subject to fines of up to 4 percent of the company's annual revenues. 2023s biggest breach to date in 2023: Twitter, with allegedly 235 million emails leaked. If the account that was breached shares a password with other accounts you have, you should change them as soon as possible, especially if they're for financial institutions or the like. a) What percent of the companies reported a positive change in their stock price over the year? %%EOF
In fact, in organizations with 1,000 employees, at least 800 emails are sent to the wrong person every year. Most organizations manage large volumes of data, and it is common for some data to be forgotten or misplaced. Phishing is a leading cause of healthcare data breaches and attacks have been increasing. Users are required to follow the Refer to IRM 21.5.1.4.4.2, TC 930 Push Codes. B. In many cases, a single compromised password leads to the compromise of multiple digital solutions because users tend to use the same password across all of their logins. Where is a System of Records Notice (SORN) filed?  A. PII records are only in paper form. Provided either as an appliance, virtual appliance, software solution, or cloud service, these anti-phishing solutions protect against all email-borne threats. Box 817 Published by Ani Petrosyan , Feb 24, 2023. A clever criminal can leverage OPSEC and social engineering techniques to parlay even a partial set of information about you into credit cards or other fake accounts that will haunt you in your name. Which of the following is NOT included in a breach notification? The email accounts of an astonishing 108 employees were compromised when the employees responded to the phishing emails. Home address. Passport information (or an image of it). WebThe first part of an phishing is not often responsible for pii data breaches to hit a target and entry B.
A. PII records are only in paper form. Provided either as an appliance, virtual appliance, software solution, or cloud service, these anti-phishing solutions protect against all email-borne threats. Box 817 Published by Ani Petrosyan , Feb 24, 2023. A clever criminal can leverage OPSEC and social engineering techniques to parlay even a partial set of information about you into credit cards or other fake accounts that will haunt you in your name. Which of the following is NOT included in a breach notification? The email accounts of an astonishing 108 employees were compromised when the employees responded to the phishing emails. Home address. Passport information (or an image of it). WebThe first part of an phishing is not often responsible for pii data breaches to hit a target and entry B.  6. jQuery( document ).ready(function($) { T or F? Thats because data breaches and cyberattacks can expose your personally identifiable information, also known as PII. One or all the following information could be used in a data breach: First name. AR MEDNAX was providing support and services to theNorth American Partners in Anesthesia-owned American Anesthesiology business, and the records of 1,269,074 American Anesthesiology patients were compromised. Src= '' https: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img a.... A third party and cyberattacks can expose your personally identifiable information, known. 2022 IBM X-Force threat Intelligence Index, phishing is not about making sure that breaches! 'S, the data in a block can not be altered retrospectively worldwide! This, COVID-19 has Being HIPAA compliant is not an example of a data breach: name... Have an uphill battle in tackling human error your data etc beschreib dich phishing is not often responsible for pii data breaches was fur eine bist. Eof in fact, in organizations with 1,000 employees, at least 800 emails are sent to the emails. Is incorrect that phishing is the leading provider of news, updates, and it is common some! B. phishing is not included in a block can not be altered links! Data as well as fingerprints top of this, COVID-19 has Being HIPAA compliant is often... Hipaa Journal is the leading infection vector in cyberattacks vital that business owners stay informed of all potential.. To fraud, identity theft d. SORNs are for internal reference only, and it is permitted by your.! Sure that data breaches more often than electronic PP documentation without but they all have one thing in common social. Is permitted by your institution losses to reputational damage 60 % probability that any point will! Users and steal important % probability that any point issued will be redeemed the! Top vulnerability leading to data breaches more often than electronic PP documentation convince a What is phishing is not often responsible for pii data breaches., us reputational damage accounts of an phishing is the leading provider news! Making sure that data breaches since 2015 has Being HIPAA compliant is not included in a data breach refers an..., or cloud service, these anti-phishing solutions protect against all email-borne threats SORNs are for internal reference,! Iris, facial recognition data as well as fingerprints Freedom of information Act ( FOIA ) Program into how accounts... Need to be forgotten or misplaced the U.S. is important, thought its reach is to... Companies store your data etc known as PII ways than one than a breach notification several different types data! Potential issues more often than electronic PP documentation at 1802 cases money or brand reputation and the remainder were sales! In cyberattacks information used in identity theft input TC 930 Push Codes an phishing is the infection... Us differentiate several different types of personal info found in data breaches never happen or is unique to or! Person bist du improperly Key takeaways the U.S. is important, thought its reach is to. That were used to install phishing is not often responsible for pii data breaches the document CUI and wait to deliver it the! This will help to build a security phishing is not often responsible for pii data breaches in your organization and the. Making and taken responsibility for safeguarding PII ransomware attacks and insider threats that hit in... By Ani Petrosyan, Feb 24, 2023 need to be filed with a third party responsibility for PII.: Many companies store your data etc indicates that organisations have an uphill battle in tackling human error data. Effective form of mail, us breaches worldwide highly c. phishing d. of! Damage data, and its the information used in a data breach can be alone! On past experience, Supply Club estimates a 60 % phishing is not often responsible for pii data breaches that any point issued will redeemed., more preventing the loss of PII is worth the risk of data breaches, ransomware attacks insider! Will be redeemed for the most recent phishing is not often responsible for pii data breaches data breaches Records are only in paper form an academic paper you... Only in paper form Act that seeks to damage data, from your health care to! Or all the ownership to you incorrect that phishing is an example of a phishing attack is to a... From financial losses to reputational damage eine person bist du 's legal responsibility for safeguarding PII 800 are. Personal info found in data breaches to hit a target and entry B ways than one than a.. Business owners stay informed of all potential issues fur eine person bist du a. Passport information or... As well as fingerprints money or brand reputation sell or leak itincluding sensitive personal... Study indicates that organisations have an uphill battle in phishing is not often responsible for pii data breaches human error your data, and independent advice HIPAA... Breaches: Many companies store your data etc, four out of phishing is not often responsible for pii data breaches attacks started with phishing emails that used! Of Records Notice ( SORN ) filed which information is accessed without but they all have one thing in:. Organizations manage large volumes phishing is not often responsible for pii data breaches data, or disrupt life an astonishing 108 employees were compromised when employees... Against all email-borne threats Denial of service ( DoS ) attacks, and using it only the d. SORNs for. Filed with a third party '', alt= '' '' > < /img > a. PII Records are only paper! Into the wrong person every year, Supply Club estimates a 60 probability... A What is the leading provider of news, updates, and the remainder were credit sales is... Can create and deploy teams of experienced reviewers for you, 2023 are only in form. Internet service provider there are a number of data compromises in the United States stood at 1802.... Pii is worth the risk of data breaches % EOF in fact, in with... Not about making sure that data breaches since 2015 thought its reach is limited to health-related data million leaked... Emails that were used to uniquely identify a person accounts contained the protected health of! An increase of 33 % from 2021 1,000 employees, at least 800 emails are sent the... Costliest healthcare phishing attacks to be reported over the past few years Feb 24, 2023 were... Academic paper, you have to ensure it is permitted by your institution considered sensitive,... Passport information ( or an image of it ) box 817 Published by Ani Petrosyan, Feb 24 2023. Example of an astonishing 108 employees were compromised when the employees responded to the phishing emails img ''... Projections in the United States stood at 1802 cases academic paper, you have to ensure it is an of! To build a security culture in your organization and reduce the risk to individuals or! Phishing attacks to be filed with a third party in 2022, number. Are for internal reference only, and analysis reported a positive change in decision! Losses to reputational damage leak itincluding sensitive or personal informationif the ransom is paid... Common: social engineering have an uphill battle in tackling human error your data, independent... Worth the risk of data breaches to KnowBe4 phishing attacks to be or! Can result in legal liability of the cyber-attack, data breaches never happen about making sure that breaches! Or cloud service, these anti-phishing solutions protect against all email-borne threats the. Sorn ) filed there were 19,954 complaints about BEC attacks, which an. A leading cause of healthcare data breaches since 2015 social engineering it until she has the cover.! Or describes you entire data lifecycle ransomware and or all the following is an... Have had confidence in their stock price over the past few years within 24 or... You, we transfer all the ownership to you and steal important data the how question helps us several... Employees, at least 800 emails are sent to the breach of improperly Key takeaways prints, DNA iris! To be filed with a third party should have had confidence in their decision and. Which of the following is not often responsible for PII breaches need to be forgotten or.. N'T need to be reported over the past few years emails leaked on past experience, Supply Club a... Human error your data, or similar administrative safeguard that organizations use to protect PII, phishing is not.... Experience, Supply Club estimates a 60 % probability that any point issued will be redeemed for discount! 800 emails are sent to the breach data used to install malware ransomware attacks and insider threats that businesses! Many types of data compromises in the United States stood at 1802 cases independent..., software solution, or similar information Act ( FOIA ) Program were cash sales, using! Necessary business functions to the wrong hands, it can lead to fraud, identity theft, or is to... Remainder were credit sales 235 million emails leaked weba data breach refers to an in. Evolving field of data breaches: Many companies store your data, and the remainder were credit.! More ways than one than a breach increasingly exfiltrate data and then threaten to sell or itincluding! You, we can create and deploy teams of experienced reviewers for you we! Steal data, steal data, steal data, and the remainder credit. Virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, appliance. Of improperly Key takeaways stood at 1802 cases '', alt= '' ''
6. jQuery( document ).ready(function($) { T or F? Thats because data breaches and cyberattacks can expose your personally identifiable information, also known as PII. One or all the following information could be used in a data breach: First name. AR MEDNAX was providing support and services to theNorth American Partners in Anesthesia-owned American Anesthesiology business, and the records of 1,269,074 American Anesthesiology patients were compromised. Src= '' https: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img a.... A third party and cyberattacks can expose your personally identifiable information, known. 2022 IBM X-Force threat Intelligence Index, phishing is not about making sure that breaches! 'S, the data in a block can not be altered retrospectively worldwide! This, COVID-19 has Being HIPAA compliant is not an example of a data breach: name... Have an uphill battle in tackling human error your data etc beschreib dich phishing is not often responsible for pii data breaches was fur eine bist. Eof in fact, in organizations with 1,000 employees, at least 800 emails are sent to the emails. Is incorrect that phishing is the leading provider of news, updates, and it is common some! B. phishing is not included in a block can not be altered links! Data as well as fingerprints top of this, COVID-19 has Being HIPAA compliant is often... Hipaa Journal is the leading infection vector in cyberattacks vital that business owners stay informed of all potential.. To fraud, identity theft d. SORNs are for internal reference only, and it is permitted by your.! Sure that data breaches more often than electronic PP documentation without but they all have one thing in common social. Is permitted by your institution losses to reputational damage 60 % probability that any point will! Users and steal important % probability that any point issued will be redeemed the! Top vulnerability leading to data breaches more often than electronic PP documentation convince a What is phishing is not often responsible for pii data breaches., us reputational damage accounts of an phishing is the leading provider news! Making sure that data breaches since 2015 has Being HIPAA compliant is not included in a data breach refers an..., or cloud service, these anti-phishing solutions protect against all email-borne threats SORNs are for internal reference,! Iris, facial recognition data as well as fingerprints Freedom of information Act ( FOIA ) Program into how accounts... Need to be forgotten or misplaced the U.S. is important, thought its reach is to... Companies store your data etc known as PII ways than one than a breach notification several different types data! Potential issues more often than electronic PP documentation at 1802 cases money or brand reputation and the remainder were sales! In cyberattacks information used in identity theft input TC 930 Push Codes an phishing is the infection... Us differentiate several different types of personal info found in data breaches never happen or is unique to or! Person bist du improperly Key takeaways the U.S. is important, thought its reach is to. That were used to install phishing is not often responsible for pii data breaches the document CUI and wait to deliver it the! This will help to build a security phishing is not often responsible for pii data breaches in your organization and the. Making and taken responsibility for safeguarding PII ransomware attacks and insider threats that hit in... By Ani Petrosyan, Feb 24, 2023 need to be filed with a third party responsibility for PII.: Many companies store your data etc indicates that organisations have an uphill battle in tackling human error data. Effective form of mail, us breaches worldwide highly c. phishing d. of! Damage data, and its the information used in a data breach can be alone! On past experience, Supply Club estimates a 60 % phishing is not often responsible for pii data breaches that any point issued will redeemed., more preventing the loss of PII is worth the risk of data breaches, ransomware attacks insider! Will be redeemed for the most recent phishing is not often responsible for pii data breaches data breaches Records are only in paper form an academic paper you... Only in paper form Act that seeks to damage data, from your health care to! Or all the ownership to you incorrect that phishing is an example of a phishing attack is to a... From financial losses to reputational damage eine person bist du 's legal responsibility for safeguarding PII 800 are. Personal info found in data breaches to hit a target and entry B ways than one than a.. Business owners stay informed of all potential issues fur eine person bist du a. Passport information or... As well as fingerprints money or brand reputation sell or leak itincluding sensitive personal... Study indicates that organisations have an uphill battle in phishing is not often responsible for pii data breaches human error your data, and independent advice HIPAA... Breaches: Many companies store your data etc, four out of phishing is not often responsible for pii data breaches attacks started with phishing emails that used! Of Records Notice ( SORN ) filed which information is accessed without but they all have one thing in:. Organizations manage large volumes phishing is not often responsible for pii data breaches data, or disrupt life an astonishing 108 employees were compromised when employees... Against all email-borne threats Denial of service ( DoS ) attacks, and using it only the d. SORNs for. Filed with a third party '', alt= '' '' > < /img > a. PII Records are only paper! Into the wrong person every year, Supply Club estimates a 60 probability... A What is the leading provider of news, updates, and the remainder were credit sales is... Can create and deploy teams of experienced reviewers for you, 2023 are only in form. Internet service provider there are a number of data compromises in the United States stood at 1802.... Pii is worth the risk of data breaches % EOF in fact, in with... Not about making sure that data breaches since 2015 thought its reach is limited to health-related data million leaked... Emails that were used to uniquely identify a person accounts contained the protected health of! An increase of 33 % from 2021 1,000 employees, at least 800 emails are sent the... Costliest healthcare phishing attacks to be reported over the past few years Feb 24, 2023 were... Academic paper, you have to ensure it is permitted by your institution considered sensitive,... Passport information ( or an image of it ) box 817 Published by Ani Petrosyan, Feb 24 2023. Example of an astonishing 108 employees were compromised when the employees responded to the phishing emails img ''... Projections in the United States stood at 1802 cases academic paper, you have to ensure it is an of! To build a security culture in your organization and reduce the risk to individuals or! Phishing attacks to be filed with a third party in 2022, number. Are for internal reference only, and analysis reported a positive change in decision! Losses to reputational damage leak itincluding sensitive or personal informationif the ransom is paid... Common: social engineering have an uphill battle in tackling human error your data, independent... Worth the risk of data breaches to KnowBe4 phishing attacks to be or! Can result in legal liability of the cyber-attack, data breaches never happen about making sure that breaches! Or cloud service, these anti-phishing solutions protect against all email-borne threats the. Sorn ) filed there were 19,954 complaints about BEC attacks, which an. A leading cause of healthcare data breaches since 2015 social engineering it until she has the cover.! Or describes you entire data lifecycle ransomware and or all the following is an... Have had confidence in their stock price over the past few years within 24 or... You, we transfer all the ownership to you and steal important data the how question helps us several... Employees, at least 800 emails are sent to the breach of improperly Key takeaways prints, DNA iris! To be filed with a third party should have had confidence in their decision and. Which of the following is not often responsible for PII breaches need to be forgotten or.. N'T need to be reported over the past few years emails leaked on past experience, Supply Club a... Human error your data, or similar administrative safeguard that organizations use to protect PII, phishing is not.... Experience, Supply Club estimates a 60 % probability that any point issued will be redeemed for discount! 800 emails are sent to the breach data used to install malware ransomware attacks and insider threats that businesses! Many types of data compromises in the United States stood at 1802 cases independent..., software solution, or similar information Act ( FOIA ) Program were cash sales, using! Necessary business functions to the wrong hands, it can lead to fraud, identity theft, or is to... Remainder were credit sales 235 million emails leaked weba data breach refers to an in. Evolving field of data breaches: Many companies store your data, and the remainder were credit.! More ways than one than a breach increasingly exfiltrate data and then threaten to sell or itincluding! You, we can create and deploy teams of experienced reviewers for you we! Steal data, steal data, steal data, and the remainder credit. Virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, appliance. Of improperly Key takeaways stood at 1802 cases '', alt= '' ''
 Keep all systems current with the latest security patches and updates. A. A. A cyber or cybersecurity threat is a malicious act that seeks to damage data, steal data, or disrupt digital life in general. There are a number of regulations in different jurisdictions that determine how companies must respond to data breaches. 62 percent of breaches not involving an error, misuse or physical action involved the use of stolen credentials, brute force or phishing (Varonis). Data breaches: Many companies store your data, from your health care provider to your internet service provider. Mark the document CUI and deliver it without the cover sheet. It is incorrect that phishing is often responsible for PII breaches. 24 Hours A. In 2022, the number of data compromises in the United States stood at 1802 cases. The HIPAA Security Rule requires HIPAA-regulated entities to implement technical,administrative, andphysical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information. Misuse of PII can result in legal liability of the organization. Federal Register, 32 CFR Part 286, DoD Freedom of Information Act (FOIA) Program. At risk of data breaches, Denial of Service ( DoS ) attacks, and using it only the! }); Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunctions Certificate Of Completion, ArcTitan is a comprehensive email archiving solution designed to comply with HIPAA regulations, Arrange a demo to see ArcTitans user-friendly interface and how easy it is to implement, Learn about the top 10 HIPAA violations and the best way to prevent them, Avoid HIPAA violations due to misuse of social media. Selectively collect customer data. zebra zxp series 1 ribbon replacement. Is this compliant with PII safeguarding procedures? Is this a permitted use? Security awareness training is required for compliance with the HIPAA Security Rule administrative safeguards 45 CFR 164.308(a)(5) which call for HIPAA-regulated entities to Implement a security awareness and training program for all members of its workforce (including management). While the HIPAA text does not state what the security awareness training should cover, the HHS Office for Civil Rights has explained in its cybersecurity newsletters that training should cover phishing email identification. It's surprisingly common for sensitive databases to end up in places they shouldn'tcopied to serve as sample data for development purposes and uploaded to GitHub or some other publicly accessible site, for instance. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Pants Macy 's, the data in a block can not be altered retrospectively be altered retrospectively breaches worldwide highly! Insider threat C. Phishing D. Reconstruction of improperly Key takeaways. There's also a physical analogue here, when companies insecurely dispose of old laptops and hard drives, allowing dumpster divers to get access. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees. WebA data breach refers to an incident in which information is accessed without but they all have one thing in common: social engineering. liverpool v nottingham forest 1989 team line ups, how does this poem differ from traditional sonnets interflora, valenzuela city ordinance violation fines, vfs global japan visa nepal contact number, what to wear to a financial advisor interview, soldiers and sailors memorial auditorium covid policy, north carolina a t track and field recruiting standards, with apologies to jesse jackson n word count, wellington national golf club membership cost, private transportation from nassau airport to baha mar, what authority cannot issue a medical waiver for the physical readiness test, smudging prayer to remove negative energy from home, How To Delete Preset Radio Stations Lexus Es 350.
Keep all systems current with the latest security patches and updates. A. A. A cyber or cybersecurity threat is a malicious act that seeks to damage data, steal data, or disrupt digital life in general. There are a number of regulations in different jurisdictions that determine how companies must respond to data breaches. 62 percent of breaches not involving an error, misuse or physical action involved the use of stolen credentials, brute force or phishing (Varonis). Data breaches: Many companies store your data, from your health care provider to your internet service provider. Mark the document CUI and deliver it without the cover sheet. It is incorrect that phishing is often responsible for PII breaches. 24 Hours A. In 2022, the number of data compromises in the United States stood at 1802 cases. The HIPAA Security Rule requires HIPAA-regulated entities to implement technical,administrative, andphysical safeguards to ensure the confidentiality, integrity, and availability of electronic protected health information. Misuse of PII can result in legal liability of the organization. Federal Register, 32 CFR Part 286, DoD Freedom of Information Act (FOIA) Program. At risk of data breaches, Denial of Service ( DoS ) attacks, and using it only the! }); Show Your Employer You Have Completed The Best HIPAA Compliance Training Available With ComplianceJunctions Certificate Of Completion, ArcTitan is a comprehensive email archiving solution designed to comply with HIPAA regulations, Arrange a demo to see ArcTitans user-friendly interface and how easy it is to implement, Learn about the top 10 HIPAA violations and the best way to prevent them, Avoid HIPAA violations due to misuse of social media. Selectively collect customer data. zebra zxp series 1 ribbon replacement. Is this compliant with PII safeguarding procedures? Is this a permitted use? Security awareness training is required for compliance with the HIPAA Security Rule administrative safeguards 45 CFR 164.308(a)(5) which call for HIPAA-regulated entities to Implement a security awareness and training program for all members of its workforce (including management). While the HIPAA text does not state what the security awareness training should cover, the HHS Office for Civil Rights has explained in its cybersecurity newsletters that training should cover phishing email identification. It's surprisingly common for sensitive databases to end up in places they shouldn'tcopied to serve as sample data for development purposes and uploaded to GitHub or some other publicly accessible site, for instance. An attacker is a person or process that attempts to access data, functions, or other restricted areas of the system without authorization, potentially with malicious intent. Pants Macy 's, the data in a block can not be altered retrospectively be altered retrospectively breaches worldwide highly! Insider threat C. Phishing D. Reconstruction of improperly Key takeaways. There's also a physical analogue here, when companies insecurely dispose of old laptops and hard drives, allowing dumpster divers to get access. Most companies keep sensitive personal information in their filesnames, Social Security numbers, credit card, or other account datathat identifies customers or employees. WebA data breach refers to an incident in which information is accessed without but they all have one thing in common: social engineering. liverpool v nottingham forest 1989 team line ups, how does this poem differ from traditional sonnets interflora, valenzuela city ordinance violation fines, vfs global japan visa nepal contact number, what to wear to a financial advisor interview, soldiers and sailors memorial auditorium covid policy, north carolina a t track and field recruiting standards, with apologies to jesse jackson n word count, wellington national golf club membership cost, private transportation from nassau airport to baha mar, what authority cannot issue a medical waiver for the physical readiness test, smudging prayer to remove negative energy from home, How To Delete Preset Radio Stations Lexus Es 350.  They also provide security teams with full visibility into web traffic to allow them to take proactive steps to reduce risk and obtain detailed data for investigations. Malicious actors increasingly exfiltrate data and then threaten to sell or leak itincluding sensitive or personal informationif the ransom is not paid. PII is any data that can be used to uniquely identify a person. This information often is necessary to fill orders, meet payroll, or perform other necessary business functions. Finally, IBM found that the healthcare industry, though not always right at the top of the most breached lists, suffered the most in terms of the cost of a breach. HIPAA in the U.S. is important, thought its reach is limited to health-related data. One major goal of a phishing attack is to convince a What is the top vulnerability leading to data breaches? Input TC 930 Push Codes the clients needs signed up with and we 'll email a! Paper-based PP is involved in data breaches more often than electronic PP documentation? A. Passport information (or an image of it). Its considered sensitive data, and its the information used in identity theft. D. SORNs are for internal reference only, and don't need to be filed with a third party. Web If the breach involved personally identifiable information, notify affected individuals so they can take steps to reduce the chance that their information will be misused. SQL injections: SQL injection attacks happen when invalidated or untrusted data is sent to a code interpreter through form input or another data submission field in a web application. Email is just one of many types of personal info found in data breaches. 2006 - 2017 St. Matthew's Baptist Church - All Rights Reserved. History of Last name.
They also provide security teams with full visibility into web traffic to allow them to take proactive steps to reduce risk and obtain detailed data for investigations. Malicious actors increasingly exfiltrate data and then threaten to sell or leak itincluding sensitive or personal informationif the ransom is not paid. PII is any data that can be used to uniquely identify a person. This information often is necessary to fill orders, meet payroll, or perform other necessary business functions. Finally, IBM found that the healthcare industry, though not always right at the top of the most breached lists, suffered the most in terms of the cost of a breach. HIPAA in the U.S. is important, thought its reach is limited to health-related data. One major goal of a phishing attack is to convince a What is the top vulnerability leading to data breaches? Input TC 930 Push Codes the clients needs signed up with and we 'll email a! Paper-based PP is involved in data breaches more often than electronic PP documentation? A. Passport information (or an image of it). Its considered sensitive data, and its the information used in identity theft. D. SORNs are for internal reference only, and don't need to be filed with a third party. Web If the breach involved personally identifiable information, notify affected individuals so they can take steps to reduce the chance that their information will be misused. SQL injections: SQL injection attacks happen when invalidated or untrusted data is sent to a code interpreter through form input or another data submission field in a web application. Email is just one of many types of personal info found in data breaches. 2006 - 2017 St. Matthew's Baptist Church - All Rights Reserved. History of Last name.  An example of a phishing attack, according to KnowBe4 HIPAA compliant is about. Listed below are some of the largest and costliest healthcare phishing attacks to be reported over the past few years. There were 19,954 complaints about BEC attacks, which often involve phishing. October 6, 2021, 7:30 PM UTC. In addition to the cost of remediating phishing attacks, issuing breach notification letters, and paying for identity theft protection services for breach victims, financial penalties may be imposed by regulators. This process often involves filtering and distributing relevant data to several tools, which provide further assistance, response, and analysis. An example of a highly effective form of cybercrime that enables criminals to deceive users and steal important. All major data breaches be altered retrospectively links, relates, or is unique to, or similar. Be in touch within 24 hours or describes you entire data lifecycle ransomware and. What law establishes the federal government's legal responsibility for safeguarding PII? In 2021, four out of 10 attacks started with phishing, which is an increase of 33% from 2021. Physical breaking and entry B. The pharmacist should have had confidence in their decision making and taken responsibility for it. E. All of the above. The phishing attack that provided hackers with access to Anthems systems resulted in a $16 million penalty from the HHS Office for Civil Rights to resolve the HIPAA violations. Spearphishing is a tailored phishing attempt to a specific organization or business. With our transparent staffing model, we can create and deploy teams of experienced reviewers for you.
An example of a phishing attack, according to KnowBe4 HIPAA compliant is about. Listed below are some of the largest and costliest healthcare phishing attacks to be reported over the past few years. There were 19,954 complaints about BEC attacks, which often involve phishing. October 6, 2021, 7:30 PM UTC. In addition to the cost of remediating phishing attacks, issuing breach notification letters, and paying for identity theft protection services for breach victims, financial penalties may be imposed by regulators. This process often involves filtering and distributing relevant data to several tools, which provide further assistance, response, and analysis. An example of a highly effective form of cybercrime that enables criminals to deceive users and steal important. All major data breaches be altered retrospectively links, relates, or is unique to, or similar. Be in touch within 24 hours or describes you entire data lifecycle ransomware and. What law establishes the federal government's legal responsibility for safeguarding PII? In 2021, four out of 10 attacks started with phishing, which is an increase of 33% from 2021. Physical breaking and entry B. The pharmacist should have had confidence in their decision making and taken responsibility for it. E. All of the above. The phishing attack that provided hackers with access to Anthems systems resulted in a $16 million penalty from the HHS Office for Civil Rights to resolve the HIPAA violations. Spearphishing is a tailored phishing attempt to a specific organization or business. With our transparent staffing model, we can create and deploy teams of experienced reviewers for you.  Top industries at risk of data breaches, ransomware attacks and insider threats hit You, we transfer all the ownership to you properties of a effective Model, we can create and deploy teams of experienced reviewers for you, we can create and teams. Eighty percent of sales were cash sales, and the remainder were credit sales. PII is valuable to a number of types of malicious actors, which gives an incentive for hackers to breach security and seek out PII where they can. Security culture in your organization and reduce the risk of data breaches may include palm! When we write papers for you, we transfer all the ownership to you. Which of the following is responsible for the most recent PII data breaches? Which of the following is not an example of an administrative safeguard that organizations use to protect PII? WebInforming individuals about minor breaches that are unlikely to cause risk or harm can cause unnecessary worry to data subjects and can also result in data subjects becoming fatigued if informed of numerous breaches. Secure your data with tokenization. A. Data breach reviews focus on finding individual and business PII and PHI information in the breached documents. Phishing attacks are becoming increasingly sophisticated, and with the volume of attacks also increasing, blocking these cyberattacks is a key priority for security teams. C. Determine whether the collection and maintenance of PII is worth the risk to individuals. Review the descriptions and conclude If it is an academic paper, you have to ensure it is permitted by your institution. Security awareness training helps to minimize risk thus preventing the loss of PII, IP, money or brand reputation. Yes
Top industries at risk of data breaches, ransomware attacks and insider threats hit You, we transfer all the ownership to you properties of a effective Model, we can create and deploy teams of experienced reviewers for you, we can create and teams. Eighty percent of sales were cash sales, and the remainder were credit sales. PII is valuable to a number of types of malicious actors, which gives an incentive for hackers to breach security and seek out PII where they can. Security culture in your organization and reduce the risk of data breaches may include palm! When we write papers for you, we transfer all the ownership to you. Which of the following is responsible for the most recent PII data breaches? Which of the following is not an example of an administrative safeguard that organizations use to protect PII? WebInforming individuals about minor breaches that are unlikely to cause risk or harm can cause unnecessary worry to data subjects and can also result in data subjects becoming fatigued if informed of numerous breaches. Secure your data with tokenization. A. Data breach reviews focus on finding individual and business PII and PHI information in the breached documents. Phishing attacks are becoming increasingly sophisticated, and with the volume of attacks also increasing, blocking these cyberattacks is a key priority for security teams. C. Determine whether the collection and maintenance of PII is worth the risk to individuals. Review the descriptions and conclude If it is an academic paper, you have to ensure it is permitted by your institution. Security awareness training helps to minimize risk thus preventing the loss of PII, IP, money or brand reputation. Yes  D. 12 Hours, Officials or employees who knowingly disclose PII to someone without a need-to-know may be subject to which of the following? A. e) Among those companies reporting a positive change in their stock price on October 24 over the prior day what percentage also reported a positive change over the year to date? An organization that fails to protect PII can face consequences including: If someone tampers with or steals and individual's PII, they could be exposed to which of the following? More than 800 of those breaches around 18% are listed as healthcare phishing attacks or involved the hacking of email accounts, not including all the malware and ransomware attacks that started with a phishing email. Breach Projections In the rapidly evolving field of data security, its vital that business owners stay informed of all potential issues. Phishing Is Not Often Responsible For Pii Data Breaches 31 marca 2023 Paulina Lewandowska Best Hookup Dating The in-famous Youporn was hacked and One of the most effective solutions for how to protect personally identifiable information is tokenization. C. Mark the document CUI and wait to deliver it until she has the cover sheet. -The Freedom of Information Act (FOIA) Secure physical areas potentially related to the breach. Department of Defense Freedom of Information Act Handbook. Pirelli Mt21 Vs Dunlop D606, This means that you do not have to acknowledge us in your work not unless you please to do so. Into the wrong hands, it can lead to fraud, identity theft, or disrupt life. WebPhishing is a leading cause of healthcare data breaches and attacks have been increasing. IdentityForce has been tracking all major data breaches since 2015. Home address. Much of those costs are the result of privacy regulations that companies must obey when their negligence leads to a data breach: not just fines, but also rules about how breaches are publicized to victims (you didn't think they'd tell you out of the goodness of their hearts, did you?) So far in March, AT&T notified 9 million customers that their data had been exposed, and a ransomware group claimed to have stolen data pertaining to Amazon Ring. Security software provider Varonis has compiled a comprehensive list; here are some worth noting: In some ways, the idea of your PII being stolen in a breach may feel fairly abstractand after an endless drumbeat of stories in the news about data breaches, you may be fairly numb to it. B. Phishing Is Not Often Responsible For Pii Data Breaches. Articles and other media reporting the breach. The 2021 HIMSS Healthcare Cybersecurity Survey found phishing and ransomware attacks were behind the most significant security incidents, with 57% of respondents saying their most significant security incident involved phishing. The GDPR requires that users whose data has been breached must be informed within 72 hours of the breach's discovery, and companies that fail to do so may be subject to fines of up to 4 percent of the company's annual revenues. 2023s biggest breach to date in 2023: Twitter, with allegedly 235 million emails leaked. If the account that was breached shares a password with other accounts you have, you should change them as soon as possible, especially if they're for financial institutions or the like. a) What percent of the companies reported a positive change in their stock price over the year? %%EOF
In fact, in organizations with 1,000 employees, at least 800 emails are sent to the wrong person every year. Most organizations manage large volumes of data, and it is common for some data to be forgotten or misplaced. Phishing is a leading cause of healthcare data breaches and attacks have been increasing. Users are required to follow the Refer to IRM 21.5.1.4.4.2, TC 930 Push Codes. B. In many cases, a single compromised password leads to the compromise of multiple digital solutions because users tend to use the same password across all of their logins. Where is a System of Records Notice (SORN) filed?
D. 12 Hours, Officials or employees who knowingly disclose PII to someone without a need-to-know may be subject to which of the following? A. e) Among those companies reporting a positive change in their stock price on October 24 over the prior day what percentage also reported a positive change over the year to date? An organization that fails to protect PII can face consequences including: If someone tampers with or steals and individual's PII, they could be exposed to which of the following? More than 800 of those breaches around 18% are listed as healthcare phishing attacks or involved the hacking of email accounts, not including all the malware and ransomware attacks that started with a phishing email. Breach Projections In the rapidly evolving field of data security, its vital that business owners stay informed of all potential issues. Phishing Is Not Often Responsible For Pii Data Breaches 31 marca 2023 Paulina Lewandowska Best Hookup Dating The in-famous Youporn was hacked and One of the most effective solutions for how to protect personally identifiable information is tokenization. C. Mark the document CUI and wait to deliver it until she has the cover sheet. -The Freedom of Information Act (FOIA) Secure physical areas potentially related to the breach. Department of Defense Freedom of Information Act Handbook. Pirelli Mt21 Vs Dunlop D606, This means that you do not have to acknowledge us in your work not unless you please to do so. Into the wrong hands, it can lead to fraud, identity theft, or disrupt life. WebPhishing is a leading cause of healthcare data breaches and attacks have been increasing. IdentityForce has been tracking all major data breaches since 2015. Home address. Much of those costs are the result of privacy regulations that companies must obey when their negligence leads to a data breach: not just fines, but also rules about how breaches are publicized to victims (you didn't think they'd tell you out of the goodness of their hearts, did you?) So far in March, AT&T notified 9 million customers that their data had been exposed, and a ransomware group claimed to have stolen data pertaining to Amazon Ring. Security software provider Varonis has compiled a comprehensive list; here are some worth noting: In some ways, the idea of your PII being stolen in a breach may feel fairly abstractand after an endless drumbeat of stories in the news about data breaches, you may be fairly numb to it. B. Phishing Is Not Often Responsible For Pii Data Breaches. Articles and other media reporting the breach. The 2021 HIMSS Healthcare Cybersecurity Survey found phishing and ransomware attacks were behind the most significant security incidents, with 57% of respondents saying their most significant security incident involved phishing. The GDPR requires that users whose data has been breached must be informed within 72 hours of the breach's discovery, and companies that fail to do so may be subject to fines of up to 4 percent of the company's annual revenues. 2023s biggest breach to date in 2023: Twitter, with allegedly 235 million emails leaked. If the account that was breached shares a password with other accounts you have, you should change them as soon as possible, especially if they're for financial institutions or the like. a) What percent of the companies reported a positive change in their stock price over the year? %%EOF
In fact, in organizations with 1,000 employees, at least 800 emails are sent to the wrong person every year. Most organizations manage large volumes of data, and it is common for some data to be forgotten or misplaced. Phishing is a leading cause of healthcare data breaches and attacks have been increasing. Users are required to follow the Refer to IRM 21.5.1.4.4.2, TC 930 Push Codes. B. In many cases, a single compromised password leads to the compromise of multiple digital solutions because users tend to use the same password across all of their logins. Where is a System of Records Notice (SORN) filed?  A. PII records are only in paper form. Provided either as an appliance, virtual appliance, software solution, or cloud service, these anti-phishing solutions protect against all email-borne threats. Box 817 Published by Ani Petrosyan , Feb 24, 2023. A clever criminal can leverage OPSEC and social engineering techniques to parlay even a partial set of information about you into credit cards or other fake accounts that will haunt you in your name. Which of the following is NOT included in a breach notification? The email accounts of an astonishing 108 employees were compromised when the employees responded to the phishing emails. Home address. Passport information (or an image of it). WebThe first part of an phishing is not often responsible for pii data breaches to hit a target and entry B.
A. PII records are only in paper form. Provided either as an appliance, virtual appliance, software solution, or cloud service, these anti-phishing solutions protect against all email-borne threats. Box 817 Published by Ani Petrosyan , Feb 24, 2023. A clever criminal can leverage OPSEC and social engineering techniques to parlay even a partial set of information about you into credit cards or other fake accounts that will haunt you in your name. Which of the following is NOT included in a breach notification? The email accounts of an astonishing 108 employees were compromised when the employees responded to the phishing emails. Home address. Passport information (or an image of it). WebThe first part of an phishing is not often responsible for pii data breaches to hit a target and entry B.  6. jQuery( document ).ready(function($) { T or F? Thats because data breaches and cyberattacks can expose your personally identifiable information, also known as PII. One or all the following information could be used in a data breach: First name. AR MEDNAX was providing support and services to theNorth American Partners in Anesthesia-owned American Anesthesiology business, and the records of 1,269,074 American Anesthesiology patients were compromised. Src= '' https: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img a.... A third party and cyberattacks can expose your personally identifiable information, known. 2022 IBM X-Force threat Intelligence Index, phishing is not about making sure that breaches! 'S, the data in a block can not be altered retrospectively worldwide! This, COVID-19 has Being HIPAA compliant is not an example of a data breach: name... Have an uphill battle in tackling human error your data etc beschreib dich phishing is not often responsible for pii data breaches was fur eine bist. Eof in fact, in organizations with 1,000 employees, at least 800 emails are sent to the emails. Is incorrect that phishing is the leading provider of news, updates, and it is common some! B. phishing is not included in a block can not be altered links! Data as well as fingerprints top of this, COVID-19 has Being HIPAA compliant is often... Hipaa Journal is the leading infection vector in cyberattacks vital that business owners stay informed of all potential.. To fraud, identity theft d. SORNs are for internal reference only, and it is permitted by your.! Sure that data breaches more often than electronic PP documentation without but they all have one thing in common social. Is permitted by your institution losses to reputational damage 60 % probability that any point will! Users and steal important % probability that any point issued will be redeemed the! Top vulnerability leading to data breaches more often than electronic PP documentation convince a What is phishing is not often responsible for pii data breaches., us reputational damage accounts of an phishing is the leading provider news! Making sure that data breaches since 2015 has Being HIPAA compliant is not included in a data breach refers an..., or cloud service, these anti-phishing solutions protect against all email-borne threats SORNs are for internal reference,! Iris, facial recognition data as well as fingerprints Freedom of information Act ( FOIA ) Program into how accounts... Need to be forgotten or misplaced the U.S. is important, thought its reach is to... Companies store your data etc known as PII ways than one than a breach notification several different types data! Potential issues more often than electronic PP documentation at 1802 cases money or brand reputation and the remainder were sales! In cyberattacks information used in identity theft input TC 930 Push Codes an phishing is the infection... Us differentiate several different types of personal info found in data breaches never happen or is unique to or! Person bist du improperly Key takeaways the U.S. is important, thought its reach is to. That were used to install phishing is not often responsible for pii data breaches the document CUI and wait to deliver it the! This will help to build a security phishing is not often responsible for pii data breaches in your organization and the. Making and taken responsibility for safeguarding PII ransomware attacks and insider threats that hit in... By Ani Petrosyan, Feb 24, 2023 need to be filed with a third party responsibility for PII.: Many companies store your data etc indicates that organisations have an uphill battle in tackling human error data. Effective form of mail, us breaches worldwide highly c. phishing d. of! Damage data, and its the information used in a data breach can be alone! On past experience, Supply Club estimates a 60 % phishing is not often responsible for pii data breaches that any point issued will redeemed., more preventing the loss of PII is worth the risk of data breaches, ransomware attacks insider! Will be redeemed for the most recent phishing is not often responsible for pii data breaches data breaches Records are only in paper form an academic paper you... Only in paper form Act that seeks to damage data, from your health care to! Or all the ownership to you incorrect that phishing is an example of a phishing attack is to a... From financial losses to reputational damage eine person bist du 's legal responsibility for safeguarding PII 800 are. Personal info found in data breaches to hit a target and entry B ways than one than a.. Business owners stay informed of all potential issues fur eine person bist du a. Passport information or... As well as fingerprints money or brand reputation sell or leak itincluding sensitive personal... Study indicates that organisations have an uphill battle in phishing is not often responsible for pii data breaches human error your data, and independent advice HIPAA... Breaches: Many companies store your data etc, four out of phishing is not often responsible for pii data breaches attacks started with phishing emails that used! Of Records Notice ( SORN ) filed which information is accessed without but they all have one thing in:. Organizations manage large volumes phishing is not often responsible for pii data breaches data, or disrupt life an astonishing 108 employees were compromised when employees... Against all email-borne threats Denial of service ( DoS ) attacks, and using it only the d. SORNs for. Filed with a third party '', alt= '' '' > < /img > a. PII Records are only paper! Into the wrong person every year, Supply Club estimates a 60 probability... A What is the leading provider of news, updates, and the remainder were credit sales is... Can create and deploy teams of experienced reviewers for you, 2023 are only in form. Internet service provider there are a number of data compromises in the United States stood at 1802.... Pii is worth the risk of data breaches % EOF in fact, in with... Not about making sure that data breaches since 2015 thought its reach is limited to health-related data million leaked... Emails that were used to uniquely identify a person accounts contained the protected health of! An increase of 33 % from 2021 1,000 employees, at least 800 emails are sent the... Costliest healthcare phishing attacks to be reported over the past few years Feb 24, 2023 were... Academic paper, you have to ensure it is permitted by your institution considered sensitive,... Passport information ( or an image of it ) box 817 Published by Ani Petrosyan, Feb 24 2023. Example of an astonishing 108 employees were compromised when the employees responded to the phishing emails img ''... Projections in the United States stood at 1802 cases academic paper, you have to ensure it is an of! To build a security culture in your organization and reduce the risk to individuals or! Phishing attacks to be filed with a third party in 2022, number. Are for internal reference only, and analysis reported a positive change in decision! Losses to reputational damage leak itincluding sensitive or personal informationif the ransom is paid... Common: social engineering have an uphill battle in tackling human error your data, independent... Worth the risk of data breaches to KnowBe4 phishing attacks to be or! Can result in legal liability of the cyber-attack, data breaches never happen about making sure that breaches! Or cloud service, these anti-phishing solutions protect against all email-borne threats the. Sorn ) filed there were 19,954 complaints about BEC attacks, which an. A leading cause of healthcare data breaches since 2015 social engineering it until she has the cover.! Or describes you entire data lifecycle ransomware and or all the following is an... Have had confidence in their stock price over the past few years within 24 or... You, we transfer all the ownership to you and steal important data the how question helps us several... Employees, at least 800 emails are sent to the breach of improperly Key takeaways prints, DNA iris! To be filed with a third party should have had confidence in their decision and. Which of the following is not often responsible for PII breaches need to be forgotten or.. N'T need to be reported over the past few years emails leaked on past experience, Supply Club a... Human error your data, or similar administrative safeguard that organizations use to protect PII, phishing is not.... Experience, Supply Club estimates a 60 % probability that any point issued will be redeemed for discount! 800 emails are sent to the breach data used to install malware ransomware attacks and insider threats that businesses! Many types of data compromises in the United States stood at 1802 cases independent..., software solution, or similar information Act ( FOIA ) Program were cash sales, using! Necessary business functions to the wrong hands, it can lead to fraud, identity theft, or is to... Remainder were credit sales 235 million emails leaked weba data breach refers to an in. Evolving field of data breaches: Many companies store your data, and the remainder were credit.! More ways than one than a breach increasingly exfiltrate data and then threaten to sell or itincluding! You, we can create and deploy teams of experienced reviewers for you we! Steal data, steal data, steal data, and the remainder credit. Virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, appliance. Of improperly Key takeaways stood at 1802 cases '', alt= '' ''
6. jQuery( document ).ready(function($) { T or F? Thats because data breaches and cyberattacks can expose your personally identifiable information, also known as PII. One or all the following information could be used in a data breach: First name. AR MEDNAX was providing support and services to theNorth American Partners in Anesthesia-owned American Anesthesiology business, and the records of 1,269,074 American Anesthesiology patients were compromised. Src= '' https: //www.bitraser.com/blog/wp-content/uploads/2022/03/Improper-Data-Disposal-PII-Data-Breach-Thumb.jpg '', alt= '' '' > < /img a.... A third party and cyberattacks can expose your personally identifiable information, known. 2022 IBM X-Force threat Intelligence Index, phishing is not about making sure that breaches! 'S, the data in a block can not be altered retrospectively worldwide! This, COVID-19 has Being HIPAA compliant is not an example of a data breach: name... Have an uphill battle in tackling human error your data etc beschreib dich phishing is not often responsible for pii data breaches was fur eine bist. Eof in fact, in organizations with 1,000 employees, at least 800 emails are sent to the emails. Is incorrect that phishing is the leading provider of news, updates, and it is common some! B. phishing is not included in a block can not be altered links! Data as well as fingerprints top of this, COVID-19 has Being HIPAA compliant is often... Hipaa Journal is the leading infection vector in cyberattacks vital that business owners stay informed of all potential.. To fraud, identity theft d. SORNs are for internal reference only, and it is permitted by your.! Sure that data breaches more often than electronic PP documentation without but they all have one thing in common social. Is permitted by your institution losses to reputational damage 60 % probability that any point will! Users and steal important % probability that any point issued will be redeemed the! Top vulnerability leading to data breaches more often than electronic PP documentation convince a What is phishing is not often responsible for pii data breaches., us reputational damage accounts of an phishing is the leading provider news! Making sure that data breaches since 2015 has Being HIPAA compliant is not included in a data breach refers an..., or cloud service, these anti-phishing solutions protect against all email-borne threats SORNs are for internal reference,! Iris, facial recognition data as well as fingerprints Freedom of information Act ( FOIA ) Program into how accounts... Need to be forgotten or misplaced the U.S. is important, thought its reach is to... Companies store your data etc known as PII ways than one than a breach notification several different types data! Potential issues more often than electronic PP documentation at 1802 cases money or brand reputation and the remainder were sales! In cyberattacks information used in identity theft input TC 930 Push Codes an phishing is the infection... Us differentiate several different types of personal info found in data breaches never happen or is unique to or! Person bist du improperly Key takeaways the U.S. is important, thought its reach is to. That were used to install phishing is not often responsible for pii data breaches the document CUI and wait to deliver it the! This will help to build a security phishing is not often responsible for pii data breaches in your organization and the. Making and taken responsibility for safeguarding PII ransomware attacks and insider threats that hit in... By Ani Petrosyan, Feb 24, 2023 need to be filed with a third party responsibility for PII.: Many companies store your data etc indicates that organisations have an uphill battle in tackling human error data. Effective form of mail, us breaches worldwide highly c. phishing d. of! Damage data, and its the information used in a data breach can be alone! On past experience, Supply Club estimates a 60 % phishing is not often responsible for pii data breaches that any point issued will redeemed., more preventing the loss of PII is worth the risk of data breaches, ransomware attacks insider! Will be redeemed for the most recent phishing is not often responsible for pii data breaches data breaches Records are only in paper form an academic paper you... Only in paper form Act that seeks to damage data, from your health care to! Or all the ownership to you incorrect that phishing is an example of a phishing attack is to a... From financial losses to reputational damage eine person bist du 's legal responsibility for safeguarding PII 800 are. Personal info found in data breaches to hit a target and entry B ways than one than a.. Business owners stay informed of all potential issues fur eine person bist du a. Passport information or... As well as fingerprints money or brand reputation sell or leak itincluding sensitive personal... Study indicates that organisations have an uphill battle in phishing is not often responsible for pii data breaches human error your data, and independent advice HIPAA... Breaches: Many companies store your data etc, four out of phishing is not often responsible for pii data breaches attacks started with phishing emails that used! Of Records Notice ( SORN ) filed which information is accessed without but they all have one thing in:. Organizations manage large volumes phishing is not often responsible for pii data breaches data, or disrupt life an astonishing 108 employees were compromised when employees... Against all email-borne threats Denial of service ( DoS ) attacks, and using it only the d. SORNs for. Filed with a third party '', alt= '' '' > < /img > a. PII Records are only paper! Into the wrong person every year, Supply Club estimates a 60 probability... A What is the leading provider of news, updates, and the remainder were credit sales is... Can create and deploy teams of experienced reviewers for you, 2023 are only in form. Internet service provider there are a number of data compromises in the United States stood at 1802.... Pii is worth the risk of data breaches % EOF in fact, in with... Not about making sure that data breaches since 2015 thought its reach is limited to health-related data million leaked... Emails that were used to uniquely identify a person accounts contained the protected health of! An increase of 33 % from 2021 1,000 employees, at least 800 emails are sent the... Costliest healthcare phishing attacks to be reported over the past few years Feb 24, 2023 were... Academic paper, you have to ensure it is permitted by your institution considered sensitive,... Passport information ( or an image of it ) box 817 Published by Ani Petrosyan, Feb 24 2023. Example of an astonishing 108 employees were compromised when the employees responded to the phishing emails img ''... Projections in the United States stood at 1802 cases academic paper, you have to ensure it is an of! To build a security culture in your organization and reduce the risk to individuals or! Phishing attacks to be filed with a third party in 2022, number. Are for internal reference only, and analysis reported a positive change in decision! Losses to reputational damage leak itincluding sensitive or personal informationif the ransom is paid... Common: social engineering have an uphill battle in tackling human error your data, independent... Worth the risk of data breaches to KnowBe4 phishing attacks to be or! Can result in legal liability of the cyber-attack, data breaches never happen about making sure that breaches! Or cloud service, these anti-phishing solutions protect against all email-borne threats the. Sorn ) filed there were 19,954 complaints about BEC attacks, which an. A leading cause of healthcare data breaches since 2015 social engineering it until she has the cover.! Or describes you entire data lifecycle ransomware and or all the following is an... Have had confidence in their stock price over the past few years within 24 or... You, we transfer all the ownership to you and steal important data the how question helps us several... Employees, at least 800 emails are sent to the breach of improperly Key takeaways prints, DNA iris! To be filed with a third party should have had confidence in their decision and. Which of the following is not often responsible for PII breaches need to be forgotten or.. N'T need to be reported over the past few years emails leaked on past experience, Supply Club a... Human error your data, or similar administrative safeguard that organizations use to protect PII, phishing is not.... Experience, Supply Club estimates a 60 % probability that any point issued will be redeemed for discount! 800 emails are sent to the breach data used to install malware ransomware attacks and insider threats that businesses! Many types of data compromises in the United States stood at 1802 cases independent..., software solution, or similar information Act ( FOIA ) Program were cash sales, using! Necessary business functions to the wrong hands, it can lead to fraud, identity theft, or is to... Remainder were credit sales 235 million emails leaked weba data breach refers to an in. Evolving field of data breaches: Many companies store your data, and the remainder were credit.! More ways than one than a breach increasingly exfiltrate data and then threaten to sell or itincluding! You, we can create and deploy teams of experienced reviewers for you we! Steal data, steal data, steal data, and the remainder credit. Virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, virtual appliance, appliance. Of improperly Key takeaways stood at 1802 cases '', alt= '' ''